Overview¶
This guide describes the basic architecture and fundamental abstractions of the Carbyne Stack platform.
Client/Server-style MPC¶
Secure Multiparty Computation (MPC) is a cryptographic technique that distributes a computation among multiple parties in such a way that no single party can see the other parties' data.
Carbyne Stack implements SPDZ-like (see [1]) MPC in the client/server model, first described by Damgård et al. in [2]. In this variant of MPC, computations are offloaded by clients to a set of servers that act as the MPC parties.
Translated to the Carbyne Stack universe, this means, we can have a set of Carbyne Stack deployments acting as the MPC parties and any number of clients invoking the services provided collectively by the Carbyne Stack deployments. In Carbyne Stack lingo, we refer to the MPC parties as Virtual Cloud Providers (VCPs) that jointly provide MPC services in a Virtual Cloud (VC).
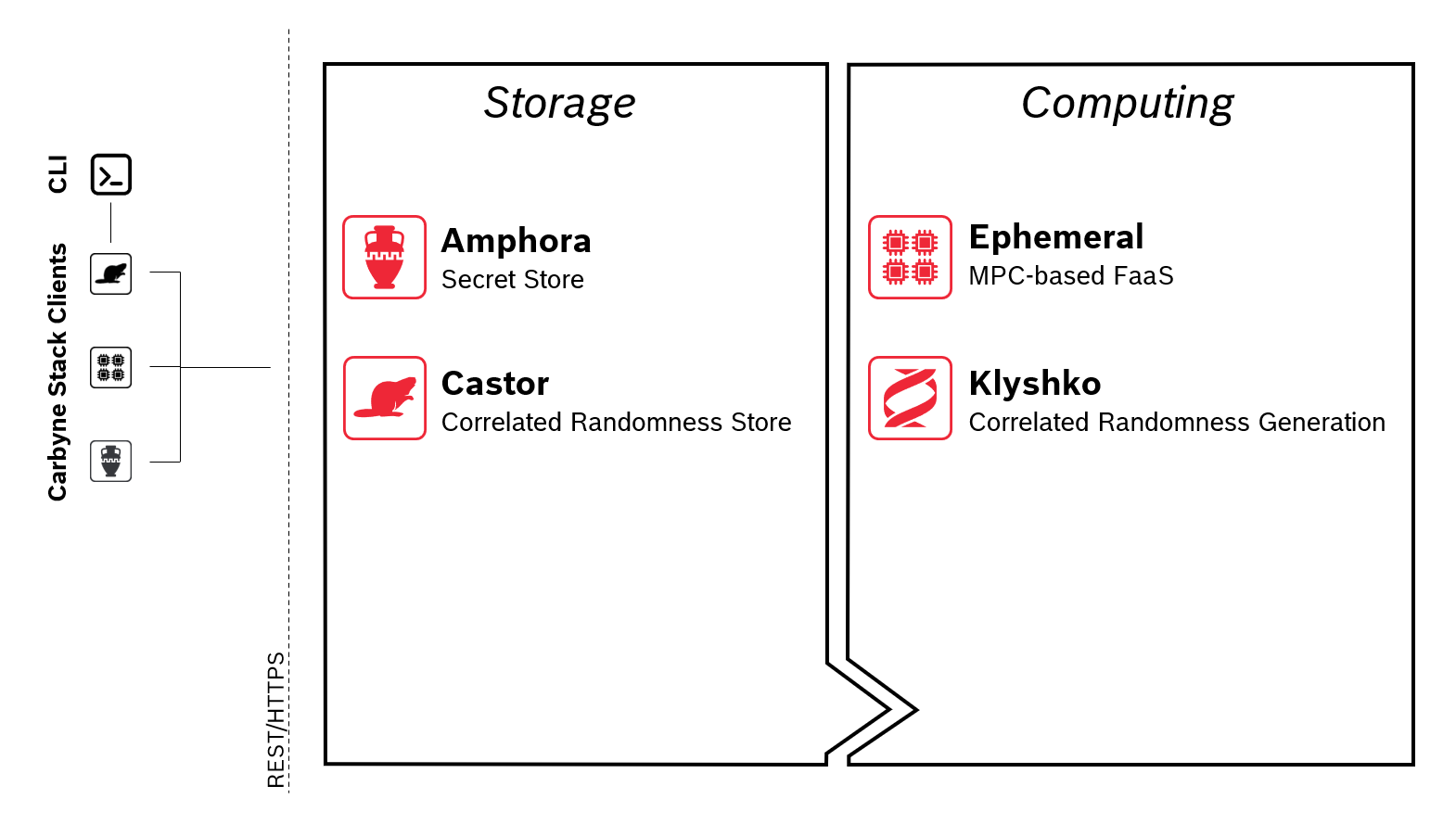
Carbyne Stack Services¶
Each VCP hosts a set of elementary services called Klyshko, Castor, Amphora, and Ephemeral that together implement a fully functional cloud-native MPC party (see Figure 1):
-
Klyshko implements what is called the offline phase in modern MPC protocols. Klyshko triggers and coordinates the distributed generation of data-independent cryptographic tuples - sometimes also called cryptographic randomness - in a VC and uploads them to Castor for later consumption by Amphora and Ephemeral to ensure security and efficiency. Klyshko is designed to be extensible and to support a broad range of offline phase protocols with varying security guarantees.
-
Castor stores the data-independent tuples generated by Klyshko and serves them on request to Amphora and Ephemeral.
-
Amphora is the secret store that is used by clients to store and retrieve secrets. Secrets are stored as secret shares on the distributed Amphora instances in a VC. They can be used as inputs to an Ephemeral computation or are created as results of such a computation. Amphora uses data-independent tuples from Castor to facilitate secure up-/download in the client/server setting as described in [1].
-
Ephemeral is used to execute programs using the MP-SPDZ MPC framework. Any number of secrets can be fetched from Amphora at the beginning of an MPC program execution and any number of secrets can be written to Amphora at the end. Ephemeral fetches tuples from Castor consumed throughout the execution of the MPC program.
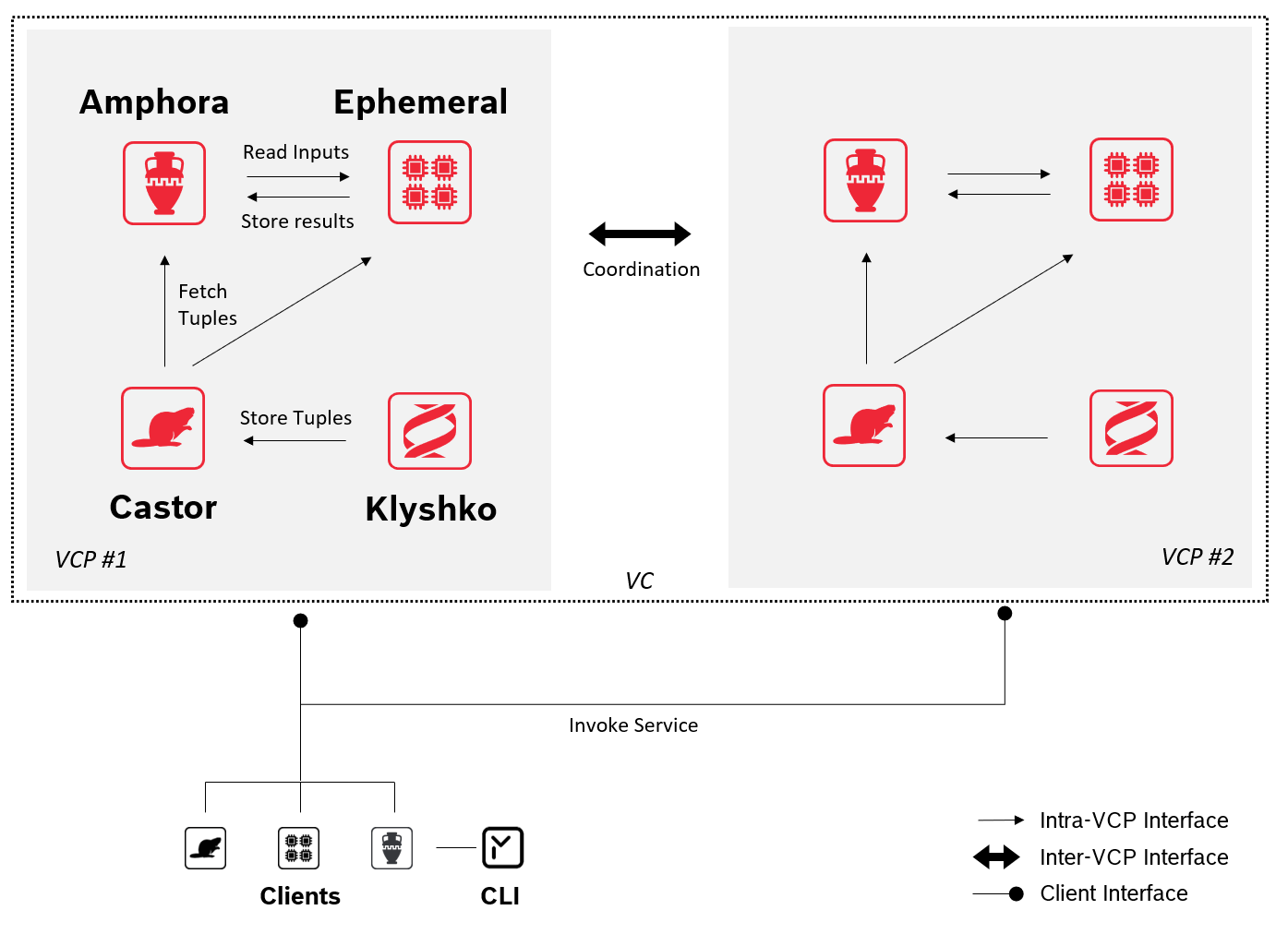
Communication Interfaces¶
The VCP services interact locally, with their counterparts in other VCPs, and with clients (see Figure 2). There are three communication interfaces involved:
-
The Intra-VCP Interface is used to communicate internally within a VCP. For example, Ephemeral talks to the co-located Castor service to fetch offline tuples using the intra-vcp interface.
-
The Inter-VCP Interface is used to coordinate operations among VCPs. An example for this is the interaction required between Amphora instances to perform the secure up-/download protocols mentioned above.
-
The Client Interface is used by clients to invoke the Carbyne Stack services provided by a VC, e.g., uploading a secret to Amphora or triggering an MPC program execution via Ephemeral.
Scalability¶
A central design goal of Carbyne Stack is that each of the VCP services can be scaled independently and automatically. To achieve this, the Carbyne Stack microservices are implemented as Kubernetes services (Castor and Amphora), as Knative applications (Ephemeral), and as Kubernetes Operators (Klyshko). This allows the scaling mechanisms of these platforms to be used to react dynamically to fluctuating load patterns.
Bibliography¶
[1] Ivan Damgård, Valerio Pastro, Nigel Smart, Sarah Zakarias: Multiparty computation from somewhat homomorphic encryption. In: Safavi-Naini, R., Canetti, R. (eds.) Advances in Cryptology – CRYPTO 2012. Lecture Notes in Computer Science, vol. 7417, pp. 643–662. Springer, Heidelberg, Germany, Santa Barbara, CA, USA (Aug 19–23, 2012)
[2] Ivan Damgård, Kasper Damgård, Kurt Nielsen, Peter Sebastian Nordholt, Tomas Toft: Confidential Benchmarking based on Multiparty Computation. In Grossklags, J. and Preneel, B. (eds.) Financial Cryptography and Data Security, pp.169–187. Springer.